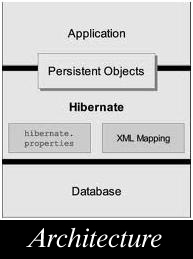
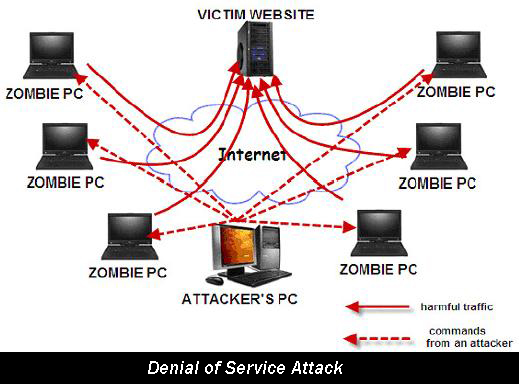
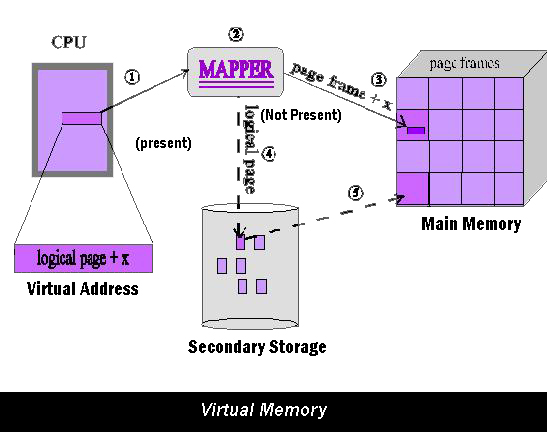
This article gives the information of data mining. The analysis becomes more meaningful using Data Mining, as it enables managers to establish relationship between business elements and find out aspects and facts about their business that may not be evident otherwise. Data mining, thus, a is an information analysis tool that involves the automated discovery of patterns and relationship in a data ware house. Data Mining is a new but […]