In this article we will study about Penetration Testing. Basically Penetration Testing is a methodology use for exploiting the system for making the system more secure. Penetration Testing is generally used in many IT companies for finding out the loopholes in their systems and recovering them them for making their systems more penetrable to the outsiders attack. Penetration Testing is also known as:-
1) Pen Test.
2)Ethical Hacking.
3)White-Hat
A penetration test is a method of evaluating security of a computer system or network by intruders which are external and internal intruders. The process involves continuous analysis for potential vulnerabilities that could result in poor system configuration.
==>Why Penetration Testing is needed?
-It is used for identifying the vulnerabilities that could result in higher risk to the system.
-It is used for identifying vulnerabilities that may be difficult to detect in network.
-It is used for testing the ability of network defenders to successfully detect the attacks.
==>What is the output of Penetration Testing?
-Output of Penetration Testing is generally weaknesses or vulnerabilities found in the system and solutions and recommendations to solve the problem.
==>Types Of Testing:-
1)Black Box Testing.
2)White Box Testing.
3)Gray Box Testing.
1)Black Box Testing:-
-Black Box Testing /External Testing accesses the network from remote location and is not concerned with internal structure of the system.
-IT Auditor concerned with Black Box Testing is known as black-hat.
2)White Box Testing:-
White Box Testing/Internal Testing is done by White-hat auditor which knows all the internal functionality of the system and the target environment. White Box Testing will remove all the internal disputes of the system/target environment .
3)Gray Box Testing:-
Gray Box Testing is the combination of both Black Box Testing and White Box Testing. The auditor engaged with Gray Box Testing is known as Gray-hat.
==>Tool used for Penetration Testing:-
Backtrack is a tool used for carrying out a penetration testing.
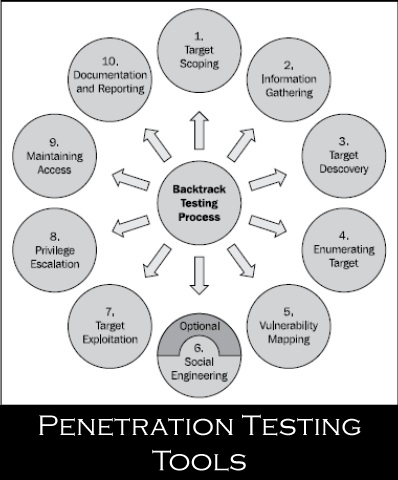
Following are the Backtrack Testing Steps as shown in above fig:-
1)Target Scoping:- It consists of certain questions
-What has to be tested?
-How it should be tested?
-What conditions to be applied during testing?
-What business objective will be achieved?
2)Information gathering:-
Information gathering process done by an auditor or pen tester uses resources that are available to understand more about the target environment. If more information is gathered there are more chances of penetration testing and more chances of Exploitation.
3)Target Discovery:-
Identify the target’s OS, networking status and architecture of the system. This target discovery process gives us complete information about devices and technology used .
4)Enumerating Target:-
It is used to find out the open ports on the target system. For that nmap command is used in linux to identify the open ports of the target system. This process enables to the vulnerability identification.
5)Vulnerability Mapping:-
Used for identifying and analyzing the vulnerabilities based on disclosed ports and services.
6)Social Engineering:-
When there is no port that is open for the attack human attack vector is used. In this process backdoor access is used by auditor for executing the malicious code.
7)Target Exploitation:-
Backtrack advanced Exploitation tools uses target acquisition:-
-per-exploitation
-exploitation and
-post exploitation
8)Privilege Escalation:-
According to the system environment privileges can also be changed using local exploits.
9)Maintaining Access:-
In this process auditor is asked to maintain access to the system for some time period. It is used for observing how an attacker can maintain access without any noisy behavior.
10)Documentation and Report:-
Preparing documents,reporting and presenting the vulnerabilities found which will be verified and hence we can conclude the penetration testing process.
In this way Backtrack 5 is one of the powerful tool used for Penetration Testing Process in IT organization to ensure the security of the system.