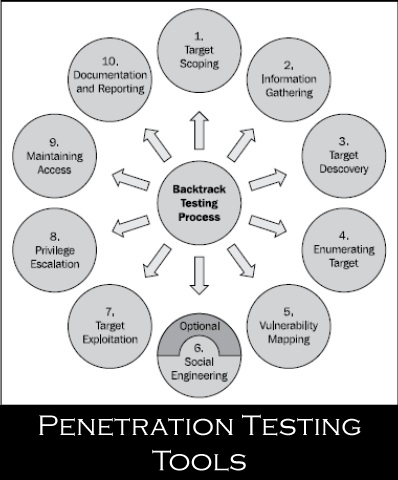
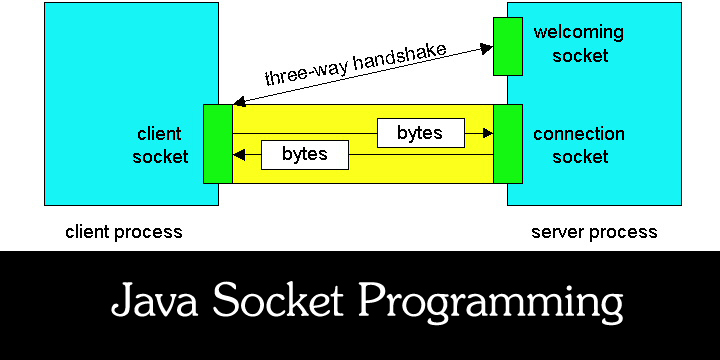
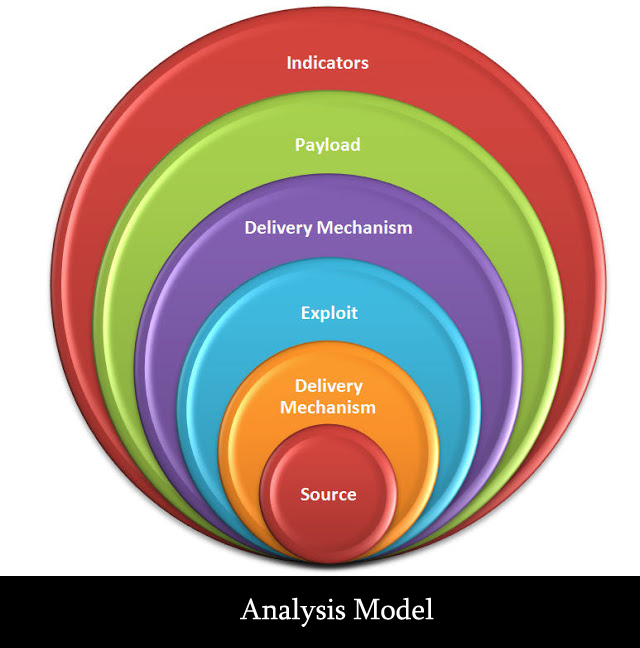
What is Software Piracy? This article gives the broad information of software piracy. Piracy of softwares involves the use reproduction or distributed without having received the expressed permission of the software author. Software piracy can be divided in four common types. The first one is end user piracy, it occurs when the users of software installs the software on more machines then they are entitled to under their license agreements. […]