As we all know that there are many hackers, crackers all over the internet system. These hackers try to gain access to other person’s account or pc. It is difficult to catch all these hackers. But honeypot is the system that helps to catch hackers and crackers who are trying to hack others account or gain access to others pc. Honeypot is the system used on internet to trap hackers who are trying to penetrate different people’s computer system through internet. In other words we can say that honeypot is the system that can fool an attacker by making him believe that the system he is attacking is a legitimate system. When an attacker try to attack honeypot enabled system, then information of attacker such as IP address of attacker is collected. By honeypot system some methods are used to stop the attack, such as- a packet is sent to the attacker with window size zero. This packet is sent to the attacker in the form of acknowledgement. This puts the attacker in the “wait” state due to which he cannot send any further data.
There are two types of honeypots and they are-
1) Low interaction honeypots and
2) High interaction honeypots.
Low interaction honeypots– Low interaction honeypots have limited interaction and they are simple as compared to high interaction honeypots. They are simple to deploy and maintain as they have limited interaction. In low interaction honeypots, in order to track hacker you select specific operating system and services that you want to monitor. These specific services are selected so that one can monitor how the hacker crack the services. One disadvantage is that they captures a limited amount of information such as transactional data and also an experienced hacker can recognize this type of honeypot. Examples of low interaction honeypots are honeyd and facades.
Façades– Facades provide false representation of target host and when it is attacked it gathers information of attacker. They are simple and they gather a limited information of threat hence are used in small to medium sized enterprises.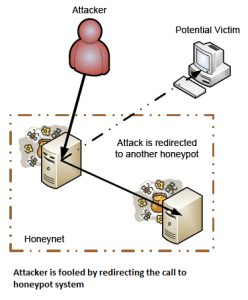
High interaction honeypots– High interaction honeypots are complex as well as they are difficult to deploy as compared to low interaction honeypots. In high interaction honeypots the nothing is emulated. A real environment is created such as real operating system and applications for example a real Linux system running a real FTP server. When an attacker attacks such a real system an extensive amount of information is collected about the attacker’s method. Examples of high interaction honeypots are honeynets and honeyd.
Honeynets- Honeynets are the best example of high interaction honeypots. Honeynet is an architecture that consist of entire network of computers specially designed to attack the system and track the threat. All activities of hacker such as emails and file uploads and SSH sessions are captured. All these activities are captured by inserting kernel modules on victim’s system.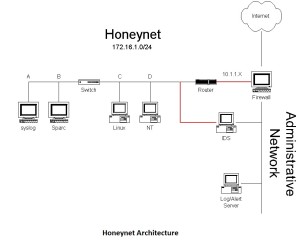
Advantages of honeypots system-
1) It is used to capture new tools used by hacker in hacking a system.
2) They are used for analyzing the attacking techniques and methods of attacker.
3) They are used for capturing extensive information about threat.
Disadvantages of honeypots system-
If honeypots are deployed with lack of planning then they can introduce risk to the existing system.